If you take one thing away from this slide, memorize this: Trusted Computing allows third parties to dictate how you can interact, on your computer, with data they send you.
Coarse grained security:
Current control over computer security is very very
coarse grained.
Suppose a server wants you to be able to view a movie (pay per
view), but not be able to make a local copy.
Ideal case for server:

However, you can do this:

By running a modified client on your computer (that emulates the client the server is expecting), you can trick the server into sending you the data and then record it locally.
Trusted computing can solve this:
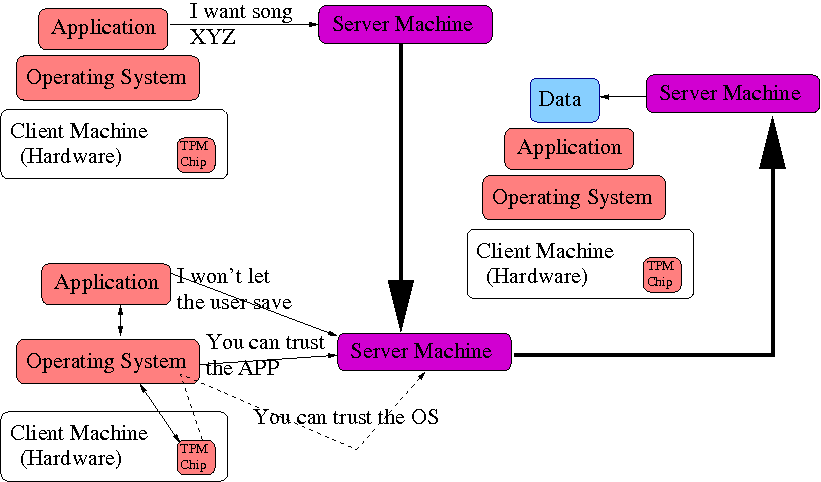
This solution, if implemented correctly, actually works. We'll explain just exactly how this works in our next (cite) section. But for now, we want to discuss the general security problem.
Control is Coarse Grained
- A server can hand you a piece of data, or a server can decide not to hand you a piece of data.
- If a server does not hand you a piece of data, you can't do anything with it.
- If a server does hand you a piece of data, you can, in theory, do anything you wish with it (may require illegal and time consuming activities such as hacking).
- You can watch this movie / listen to this song 10 times.
- You can't make a local copy.
- You can't modify it.
- You can't send it to a friend.
Problem is more than just Pay Per View:
- World of Warcraft, Online Games: I want you to use the client I send you. I don't want you peeking / poking with values in RAM. This eliminates Cheating in Online Games
- Large Corporations. I send you a confidential document. I don't want you printing it or emailing it to others.
- ... so forth ... any situation where a centralized party wants to be able to place constraints on how you deal with the data they send you.
