If you take one thing away from this slide, memorize this: Trusted Computing, if properly implemented, will allow third parties to dictate how you interact, on your computer, with data they send you.
Understanding by Attacking
To understand how Trusted Computing works, we're going to try a few common attacks (and show how they fail). Although this is not a concrete proof, it demonstrates the intuition and interested readers can read up on (cite).Review
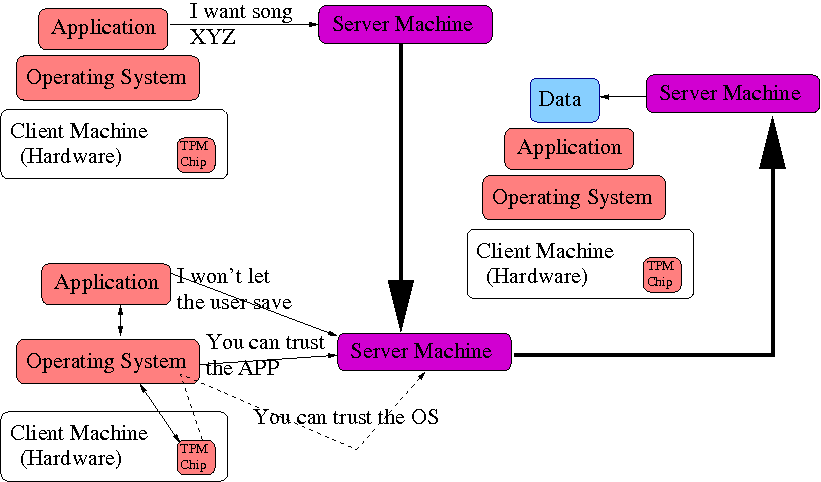
What happens here is that before the server sends over the data, the server talks to the TPM, the OS, and the Application. The TPM vouches for the OS, the OS vouches for the Application, and the Application promises to not let the user do anything with the data that the server has not granted. Maybe we can still copy the data.
Eavesdrop
Can we eavesdrop on the data?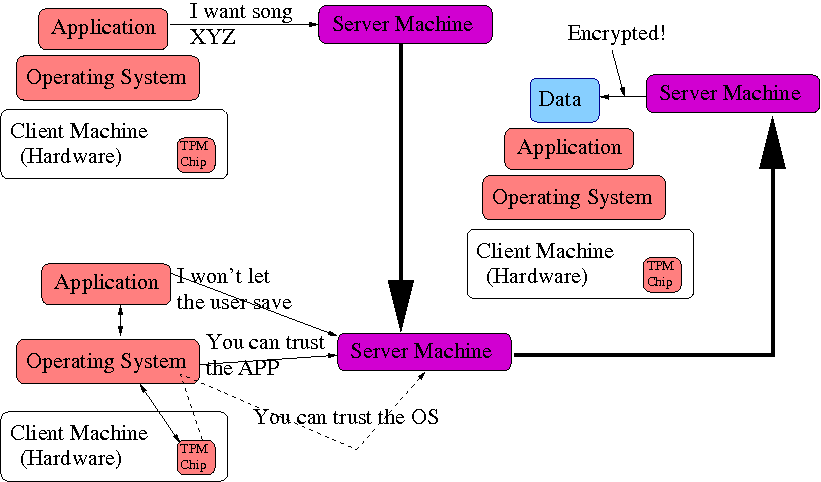
Doh! The data is encrypted.
Attack the App!
Maybe we can just modify the application like last time?
Doh! The OS tells the server that the application we're running has not been approved. Okay, we'll hack the OS too.
Attack the OS
Okay, we'll modify the OS too to say that the Application has been approved.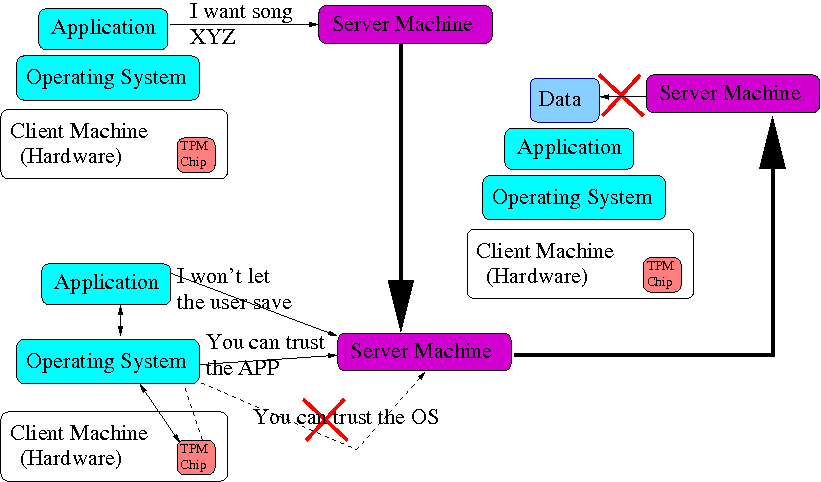
Doh! the TPM sends a message saying that the OS has not been approved.
But wait, we're about to win. The message from the TPM must go through the OS. We can change that message.
Attack TPM:
- The message from the TPM is encrypted, MAC-ed (makes it tamper proof), and is probably a challenge request -- so we can't easily modify/forge the message.
- Okay, we'll get the Endorsement Key from the TPM.
- Wait ... it's in hardware. And if we tamper with it, it's supposed to self destruct.
Sealed Storage
Sealed Storage is similar to this -- the data is encrypted, and decrypted only when a given software stack is used. By ensuring certain characterisitcs of this software stack, a third party can limit what you do with the data on your computer.The main difference is at the attestation is not to a remote server.
