The Great Firewall of China: Background
Posted: June 1, 2011 | Author: pingp | Filed under: Great Firewall of China | Leave a comment »The Great Firewall of China, also formally known as the Golden Shield Project, is the Chinese government’s internet censorship and surveillance project. Initiated, developed, and operated by the Ministry of Public Security (MPS), the project is one of the most controversial subjects in the world. While many people of the Western world treat the project as a human right violation, some countries are actually adopting China’s model. Some people think that the issue is interesting because the Chinese economy benefits tremendously from the Internet, but the Internet, in turn, is interfering with its political stability. Other people think that it is just a matter of time until Chinese communism collapses. On this website, we will provide a thorough examination of historical and technical aspects of the Great Firewall of China.
China’s Great Dilemma
The Internet came to China in 1994, under the presidency of Jiang Zemin. His decision to develop the Internet in China was heavily influenced by Alvin Toffler’s “third wave” theory, which claims that the world is moving away from the Industrial Age (second wave) to the Information Age (third wave). For China to compete with other countries, it is thus imperative that the Internet be accessible in the country. The idea of bringing in new technology to improve China’s competitive edge, however, is not new. Since 1979, Deng Xiaoping enacted the Open Door policy to bring in Western knowledge and open the country to foreign trade and investment.
After the Open Door policy was implemented, China has struggled to strike a balance between “opening up” to the Western world and keeping its people away from the Western ideology. Deng Xinaoping once said that “if you open the window for fresh air, you have to expect some flies to blow in.” In order to keep these “flies” away, the Ministry of Public Security thus initiated the Golden Shield Project in 2000. This particular project poses one of the most ironic dilemmas in modern history. On one hand, the Chinese government desires to make use of the information technology that comes with the Internet to drive its blooming economy. On the other hand, the Internet inherently encourages diversity of ideas, and is a tool for democratizing society. In other words, while the Internet is important to China’s economy, its very existence also undermines the political stability of the country. China is constantly seeking to strike the balance between these two ends.
The Golden Shield Project
Just as the Chinese government had expected, the number of internet users in China soared from nearly 0 percent in 1994, when the Internet was first introduced to the society, to 28.8 percent in 2009. While the amount of information over the last fifteen years was increased exponentially, the government is losing control the spread and availability of information. The Chinese government, however, is determined to control online content and its citizens with regard to the kinds of information to which they have accessed. MPS, the branch of the government that is deals with this issue, immediately took action by launching the Golden Shield Project.
Although MPS has been developing the Golden Shield Project sine the 1990s, the project made its first public appearance in 2000, during the Trade Show held in Beijing. Security China 2000, one of the showcases in the Trade Show, became the foundation of the Golden Shield Project. According to a report by Greg Walton, Security China 2000 aimed to promote “the adoption of advanced information and communication technology to strengthen central police control, responsiveness, and crime combating capacity, so as to improve the efficiency and effectiveness of police work.” The government initially envisioned the Golden Shield Project to be a comprehensive database-driven surveillance system that could access every citizen’s record as well as link national, regional, and local security together.
The unexpected speed of Internet expansion in China, however, necessitated various adjustments to the initial vision of the Golden Shield Project. The liberalization of the telecommunication sector bought about rapid changes in technology. This greatly reduced the project’s potential to be the system that links information from all levels, local to national. As a result of reassessment and evaluation, the Golden Shield Project now focuses on content-filtering firewalls on individuals instead – the direction that eventually earned the nickname the Great Firewall of China. In other words, the project shifted from “generalized content control at the gateway level to individual surveillance of users at the edge of the network.”
In order to develop necessary the technology for the project, the Chinese government hired teams of engineers and collaborated with many research institutes and technology providers both within the country and outside. Tsinghua University and Nortel Networks, one of the largest Canadian telecommunication technology providers, were two organizations that spearheaded the research. The main objective of this collaboration was to develop China’s networking capability. Nortel Networks, however, was not the only Western corporation that helped China develop its surveillance technology. Walton reported that Motorola provided wireless communication devices for China’s traffic police; Sun Microsystems linked all 33 provincial police departments through computer networks; and Cisco Systems provided China with routers and firewalls in the network.
Today, with its most sophisticated internet censorship program, China even exports its technology to other countries such as Cuba, Zimbabwe, and Belarus. To help you get a glimpse of what is China current censorship and firewall system is like (although we will cover the technical details in later section), we provide this short video from YouTube:
A Culture of Self Censorship
What makes the Great Firewall of China so effective (and controversial) is not only its complex technology but also the culture that the system engenders – a culture of self-censorship. The Chinese government mandates that companies be responsible for their public content. In other words, it is the job of these companies to make sure that their online portals do not contain any prohibited topics or obscenities. Leading online news media in China, such as Xinhuanet.com, Chinadaily.com.cn, Chinanews, and Baidu.com obediently follow the government’s decree, pledging that they “will make the Internet a vital publisher of scientific theories… maintain social stability, and promote the building of a socialist harmonious society.”
Transnational Internet corporations such as Google, Yahoo!, and Microsoft are also subjected to self-censorship regulations. Although censorship is very much against Western ideology, the size of the Chinese market is too profitable for the companies to bypass these opportunities. However, self-censorship does attract criticism in the Western hemisphere. For example, Google’s decision to censor some of its content to please the Chinese government is currently one of the most discussed topics in the Western media (we will also cover this in greater detail later).
The figure above shows an error message from MSN Spaces Censorship (Microsoft), which reads that “this item contains forbidden language: Please remove the forbidden language from this item.”
The above finding from an empirical study by OpenNet Initiative displays the most commonly censored words or phrases.
The Great Firewall: a technical perspective
Posted: May 30, 2011 | Author: martyhu | Filed under: Great Firewall of China | Leave a comment »How exactly does the Great Firewall Work? In this post, we’ll discuss the technical details of China’s firewall infrastructure. You’ll get to understand of some of the technology China employs as well as it’s limitations.
First, we’ll clarify some terminology and background on how the internet works. You’ll need to understand this to get through the rest of this article. If you’re already internet and tech savvy, feel free to skip ahead.
Quick Layman’s Guide to How the Internet Works:
The internet is basically a huge pile of computers. Each time you go to your favorite website (ie. facebook.com), you’re establishing a connection with that computer. The remote computer sends you some data, which you can view via your browser. You can keep the connection with the computer open as long as you need data from it.
The dirty secret of the internet is that when you go to your favorite website, you may not be going to the same computer. Why’s that? Well, depending on where it might be more convenient for you to go to a computer that’s closer to where you are. Just as if you were shopping for your groceries, you would go to a different convenience store depending on where you lived. So really, the grocery store is better identified by it’s address, rather than it’s name. There are many Ralph’s all over the country, but there is only one a block away from your home.
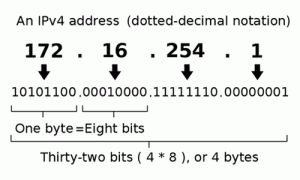
Computers are much the same way. The physical location of your favorite grocery store in the computer world is known as an IP address – a unique identifying number for every machine on the internet. Most addresses are typically IPv4, which just means that they are 32 bits in length. Here’s a typical IP address.
From reading this, you might notice that the number seems a bit random. If you did, you’d be exactly right – IP addresses are very hard to remember. So instead of using IP addresses to navigate to the computers we want, we tend to use human readable domain names, like facebook.com and google.com. The side effect to doing this is that each time we want to go to the domain name we remember we must go look up the IP address before we can connect and fetch the data we want. The machine for this is called a name server.
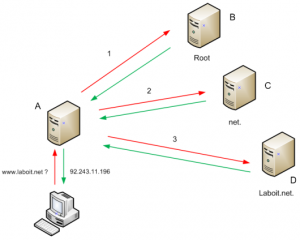
Each of the beige boxes in the above diagram is a name server. How name servers work, in essence, is as follows:
- Client gives the name server the name they remember. In this diagram, it’s laboit.net.
- Name server goes and asks some other authority name servers where to go. In the diagram, this process is labelled 1, 2, and 3.
- Name server returns the IP address. In this diagram, it’s 92.243.11.196.
The key piece to note is that every name server must depend on an authority name server, and trust falls completely on the authority name server. This becomes an interesting situation in the Chinese firewall, where the Chinese government controls all of the national authority name servers. We’ll talk more about this in a bit.
Technical Walk-through on how the Great Firewall works:
The Great Firewall uses three distinct types of methods to block access to websites in China. They are as follows:
- IP Blocking
- IP address Misdirection
- Data filtering
We’ll address each of them in turn.
IP Blocking
In this method, access to a certain IP address is refused connectivity by the Chinese firewall. This is the equivalent of preventing the user from gaining any sort of access to the remote computer, since the firewall intercepts all of the data sent and received by computers within the network.
Example:
www.facebook.com -> blocked
In the above example, facebook.com maps to a known IP address (e.g 69.63.187.17) so any connection made to that location is disconnected by the firewall.
IP address Misdirection
From our primer on name servers, we learned that the internet must basically trust all authoritative name servers to give it the correct IP addresses for a given name. However, in the case of the Great Firewall, the Chinese controls the majority of the internet presence and many of the authoritative name servers. By exploiting a flaw in the naming system, the government can redirect a given domain name to whichever actual web site it would rather have the people see. This technique is often called URL hijacking.
Example:
www.mit.edu -> (www.misdirected.mit.clone.edu)
In the above example, note that mit.edu itself is based in the United States. Since mit.edu is the actual IP address, it acts as the final arbiter as to what it’s own IP address is. However, any user from within China trying to reach ww.mit.edu will have his/her data intercepted by the Great Firewall as the request leaves China. Then, before mit.edu (which is located on the other side of the world) even sees the request, the Chinese government will issue a fake response to the original request solicitor. The naming system, which is built entirely on trust, is designed to accept this response without further asking and it goes to the fake website.
Data Filtering
The Chinese government will also examine the content of the URL that a request solicitor initiates a request with as well as the data they send inside of that request. These techniques are called URL filtering and packet filtering respectively.
Example 1:
http://www.google.com/search?aq=0&oq=tienan&sourceid=chrome&ie=UTF-8&q=tiananmen+square -> blocked
In the above example, a user initiates a Google search for “Tienanmen Square”. This creates a request URL with “tiananmen+square” in the URL, which is intercepted by the Chinese government and dropped. This is an example of URL filtering.
Example 2:
http://www.folfg.org/ -> blocked
In this case, the user navigates to a URL that doesn’t have any obviously discernible characteristic that ought to become blocked. However, the website itself contains information about Falun Gong: a system of beliefs and religious movement in China upon, which the government has relentlessly cracked down and prosecuted. The firewall, intercepting such information, would identify Falun Gong in the data and block further transmission.
This concludes the short primer on the technical aspects regarding the Great Wall. Feel free to comment and give your opinion.