SSL: Background

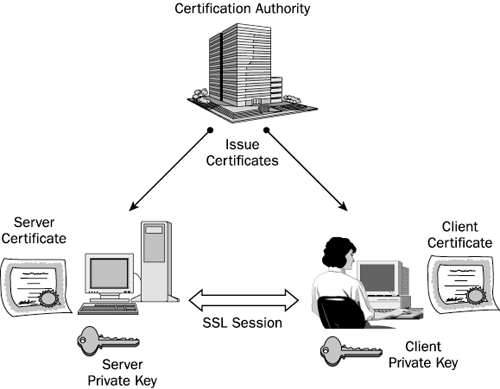
Prior to anyone accessing a website, the company who owns the secure website creates a public/private key pair and obtains a SSL certificate from a Certificate Authority (CA). The private key is used to decode the messages that are encoded with the public key. This way the website can send its public key to users to encode messages and then decode the messages with the private key. On the userís side, each userís browser has its own key, which is used for both encoding and decoding information. The trick to establishing a connection is sharing the userís key with the website. Once the website has obtained the userís key, both the user and website can encode and decode the messages that they send to one another.
When a user tries to access a webpage secured with SSL, their browser establishes a connection with the required server. However, a secure connection with the user is needed so that someone else doesnít intercept and read the data. To establish the secure connection, the website sends the user its public key. The userís browser checks with the CA to make sure that the webpage is certified and uses that public key to encode the userís key. The encoded userís key is sent to the webpage. The webpage uses its private key to decode the userís key. Since both the user and the webpage have the userís key, they can use it to encode and decode the messages that are passed between them.
An attacker intercepting any part of this process will be unable to decode the information. If the attacker intercepts the public key, it will not allow them to gain access to the userís information since it is only used to encode. If the attacker intercepts the encoded user key, they cannot decode it since only the webpage has the private key that is used to decode information. Without the user key, the attacker cannot decode any of the information that is subsequently passed between the webpage and the user.