|
|
Keystroke Logging
Brief Rundown of Technology:
Keystroke logging, a.k.a. keylogging, is simply any procedure which captures all user keystrokes to a computer system. This is especially useful in the cases where an end-user is technically savvy enough to use some kind of computer encryption. Computer cryptography has reached the point where it is virtually unbreakable. Keylogging can be used to bypass computer encryption because it records a user's input to the computer, rather than what the computer outputs.
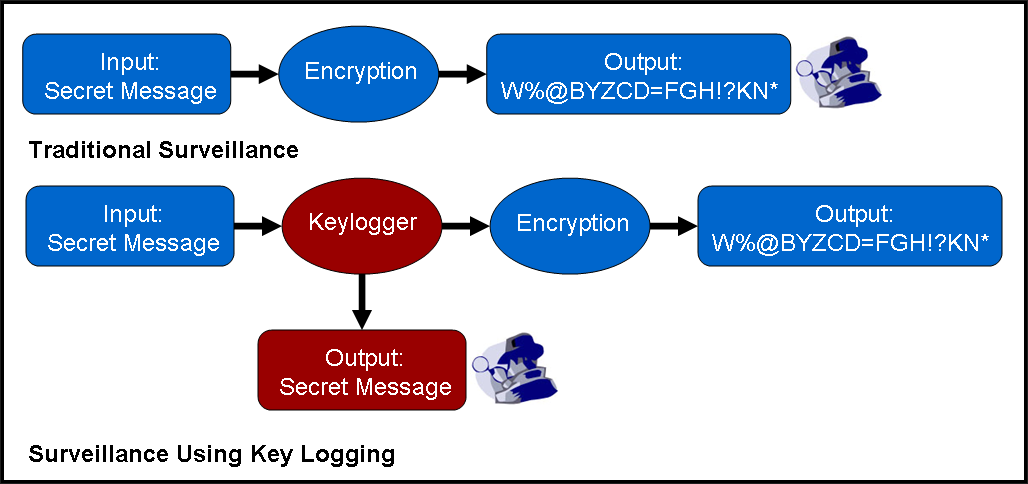
Keystroke loggers, a.k.a. keyloggers, are the actual implementations of keylogging. Keyloggers can be implemented in either hardware or software.
Hardware implementations generally have some form of internal memory which logs the keyboard's activity. Hardware keyloggers can be: 1) "Trojan" keyboards with a keylogger already built-in, 2) outside devices that must be physically installed into the original keyboard, or 3) outside devices that attach to the keyboard's cable, serving as a keyboard "wire-tap." Hardware keyloggers are impossible to detect without physical examination, but do require physical access to the machine.

Hardware keyloggers are easily purchaseable.
http://www.telephonecallrecorder.com/images/keyloggers-install.jpg
Software implementations can be done on several different levels in the computer's operating system. A software keylogger could be as simple as a top-level computer program. These programs run in the background like any other program and use a "hooking" mechanism to attach themselves to keyboard input. In Windows, this is accomplished by using the publicly available Windows function SetWindowsHookEx() to monitor all keystrokes. Since these are at the top level of computer programs, these keyloggers are relatively easy to detect.
A software keylogger could be as complex as a bottom-level kernel driver. The kernel driver is the lowest level of the operating system because it deals with the actual software interface between the input devices and the operating system. Installation of kernel driver keyloggers replaces the operating system's software for interpreting individual keystrokes. Since these are at the bottom level of the kernel, these keyloggers can be virtually impossible to detect.
Precedence/Historic Cases:
Federal bodies have a history of using keyloggers during their investigations. The most publicized case was the FBI's use of a keylogger in 1999 to gather evidence against Nicodemo Scarfo Jr., a reputed Cosa Nostra mobster. The FBI was investigating Scarfo for charges involving gambling and loan-sharking, but was having troubles due to Scarfo's use of PGP (Pretty Good Privacy), a popular encryption program that scrambles computer files so that they cannot be opened without a password. To gain access to those files, FBI agents secured a search warrant on January 1999 against Scarfo and installed a software keylogger on Scarfo's computer. Using this keylogger, the FBI was able to determine Scarfo's PGP password, allowing them to view Scarfo's encrypted files. These files contributedto the evidence required to indict Scarfo in June 2000.
The FBI has also been alleged to develop a program called "Magic Lantern." If the leaked reports are correct, Magic Lantern was a "Trojan program" which would surreptitiously install and run itself on a computer without the user's knowledge. These Trojan programs distribute themselves via infected email attachments or software downloads. Upon infiltration, Magic Lantern would then proceed to hide itself from detection and record every keystroke from that computer. The FBI has confirmed the existence of the program, but refrained from disclosing any details and maintained that it was a "workbench project" that had not actually been deployed.
Further Reading:
http://www.securityfocus.com/infocus/1829
http://www.pcworld.com/article/id,94603-page,1-c,privacysecurity/article.html
http://msdn2.microsoft.com/en-us/library/ms644990(VS.85).aspx
http://www.usatoday.com/tech/news/2001/12/27/fbi-snooping.htm
http://epic.org/crypto/scarfo/opinion.html
http://www.worldnetdaily.com/news/article.asp?ARTICLE_ID=25471
http://www.wired.com/politics/law/news/2007/07/fbi_spyware
http://www.pcworld.com/article/id,78070-page,1/article.html
|