introduction
|
worms and viruses
|
costs
|
|
who's responsible?
|
|
solutions
|
references
|
|
|
CS201 Final Project
Neil Chou
Jiayi Chong
Chee Hau Tan
|
|
Technical Solutions
Before an attacker decides on the form of attack, he or she has to decide
what forms of attack are possible. This is often done by a port scan. A
port can be thought of as a channel in which an program running on the
computer listens on for incoming network traffic. Programs can request to
listen to different ports for their own network communication
purposes. Hence, an attacker can easily tell which programs and running by
doing a port scan on the target machine. From the port scan, the attacker
can then decide on the type of attack since he has the list of vunerable
programs running on the target machine. If we are able to withhold or
prevent the attacker from obtaining such information, then it will make
attacking networked machines a lot more difficult.
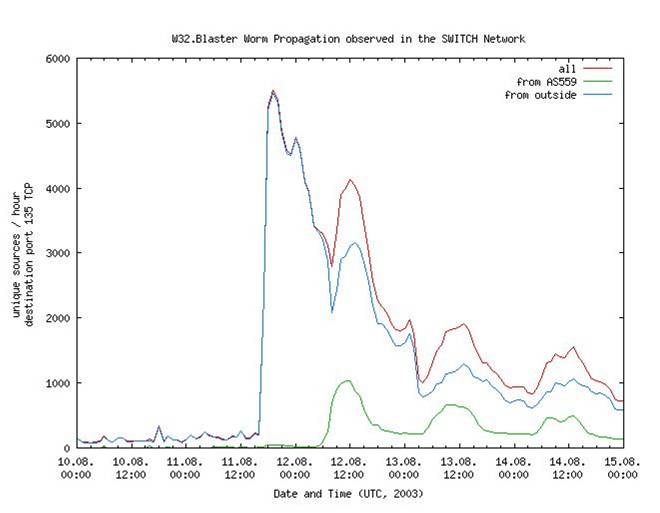
An internet worm spreads extremely quickly in the
first few minutes after it's released, and then experiences an exponential
decrease in the number of users affected after that
In addition, it is crucial for system administrators to try to curb the
spread of internet worms immediately after it has been released in order
to minimize the number of users infected, as can be seen in the graph
above.
Port Knocking
One such method is called port knocking. Port knocking is a method of
establishing a connection to a networked computer that has no open
ports. Before a connection is established, ports are opened using a port
knock sequence, which is a series of connection attempts to closed
ports. A remote host generates and sends an authentic knock sequence in
order to manipulate the server's firewall rules to open one or more
specific ports. These manipulations are mediated by a port knock daemon,
running on the server, which monitors the firewall log file for connection
attempts which can be translated into authentic knock sequences. Once the
desired ports are opened, the remote host can establish a connection and
begin a session. Another knock sequence may used to trigger the closing of
the port. An attacker will not be able to obtain or know what ports are
open on the target machine since he or she does not know the authentic
knock sequence.
Automated Patching
Automated patching will help in the problem or ignorant or lazy users. It
wil also reduce the amount of time the system administrators have to put
into patching computer systems on the network. At the same time, because
viruses and worms spread rapidly(infecting thousands of machines in less
than an hour), manual patching is often too slow to combat such a digital
epidemic. Instead, automated patching, if implemented effectively, can
match or exceed the speed at which worms and viruses propagate. This will
be crucial to prevent the further spread of viruses and worms throughout
th network. Automated patching has already been implemented by software
companies. Since the release of Windows XP and Service Pack 3 for Windows
2000, Microsoft has offered a free and automatic Operating System updating
tool, the Automatic Updates service. This service automatically connects
to either a local or Microsoft update site, downloads approved updates,
and installs the updates at a scheduled interval on the computer. The
Automatic Updates service can deploy current and future updates to
thousands of machines in minutes, instead of 15-20 minutes per machine for
a manual update.
IP Puzzles
To lower the risk of any of a DOS attack on the campus servers, one can
employ the method of IP puzzles. The general idea behind this approach
involves the server sending the client a puzzle over the network if the
client requests some form of access to the server. Valid clients will send
in a correct response to the server. Rogue clients controlled by the
attacker for the purpose of a DOS attack will not know the answer to the
puzzle, allowing the server to ignore the request from the client. This
will allow the server to actually identify which requests to it are
legitimate and which ones are the results of potential DOS attacks.
From the statistics gathered, we know that a significant percentage of
machines got broken into due to security flaws in the Windows File Sharing
network protocol.
Sandboxed Applications
Because campus servers contain private data by hundreds of users on
campus, they are ideal targets for an attack. Campus servers also run many
different types of applications to serve the various needs of their
users. Some ot these applications might contain security vunerabilities
that are open for exploit. One way to reduce this risk is to run such
applications in a sandbox. A sandbox is used to refer to a test system
which replicates (often in reduced size or capacity) the actual computing
environment for which software is being developed. The presence of such a
safe, controlled environment allows developers to try experimental code
without fear of damaging a mission-critical system. At the same time,
sandboxes also act to contain the damaged caused in the event of a
potential break-in. This will prevent the loss of personal data(like user
passwords) if we are able to separate the data from the sandboxed
application.
|

